There’s an entire supply chain economy behind cyber crime. Here’s a report by CrowdStrike that shows how cyber crime groups are connected and operate.
https://www.zdnet.com/article/this-chart-shows-the-connections-between-cybercrime-groups/
Author: Eddy K
Disinformation and Fake News
Clickbait is an article with content that is completely unrelated to it’s interesting title. This is a common way for cybercriminals to use large scale media platforms to distribute disinformation to confuse and mislead audiences.
Content could be:
Fabricated: completely untrue.
Imposter: pretending to be from a reliable source.
Misleading: presents content in a misleading way.
Manipulated: images or video that has been edited or distorted.
Context by Connection: Content that contains both facts and untrue information.
Satire or Parody: Funny or exaggerated stories that may be used to fool readers.
Always:
- Consider the reliability of the source and author. Where, when and from whom was the information retrieved from?
- Fact-Check the information that you see and educate yourself on the subject. You can use fact-checking sites such as FactCheck.org, PolitiFact.com, or Snopes.com to check the validity of content that you find.
- Only consume news from mainstream news sources.
Careful what you share on Social Media
In 2016, a group of robbers broke into Kim Kardashian West’s hotel room, bound and gagged her, and made off with more than $10 million of jewellery. Months later in 2017, police arrested 10 individuals allegedly involved in the obbery, including mastermind Aomar Ait Khedache.
In an interview, Khedache revealed that he and his cohorts had targetted Kardashian West after she posted photos of her jewelry collection and updates about her trip to Paris for fashion week on social media.
“The jewels were shown on the internet, and she said that she didn’t wear fakes. She shared the time she would arrive in France. You just had to look at the internet and you knew everything. Absolutely everything.”
Using this information, along with data from social media accounts associated with Kardashian West’s family and friends travelling with her, the theives were able to determine the best time to strike – when she was at the hotel alone after telling her bodyguard to accompany her sisters to a club for the eveniong.
The robbery triggered a brief break from social media for Kardashian West, as well as changes to how she now uses social media, including posting about her activities only after she has left the location.
Sp0t thę HomogIyph
Microsoft recently announced legal action against domains that impersonate the brand using homoglyphs. A homoglyph is a letter or character that closely resembles another letter or character. Cybercriminals use homoglyphs to trick you into thinking a domain belongs to a trusted company.
Here’s an example: Scammers could use a zero (0) in place of a capital letter “O” or they could use a lowercase letter “L” in place of a capital letter “i”. Using these examples, the bad guys can impersonate SINGPOST.COM as SINGP0ST.COM. Some cybercriminals take this method one step further by using characters from other languages. For example, the Russian character “Ь” could be used in place of an English letter “b”.
Remember the tips below:
- Be cautious when you receive an email that you were not expecting. This trick can be used to impersonate any company, brand, or even a person’s name.
- Before you click, always hover over a link to preview the destination, even if you think the email is legitimate. Pay close attention to the characters in the URL.
- If you’re asked to log in to an account or an online service, navigate to the official website and log in there. That way, you can ensure you’re logging in to the real website and not a phony look-alike website.
- A properly operating password manager will not automatically fill in your password on an impersonated website.
Tip 14: ALWAYS KEEP UPDATED
What to do:
Set your PC, tablet and mobile device to download and apply updates automatically.
Why do it?
Software isn’t perfect. Sometimes security holes exist that are found and exploited by hackers. Cybercriminals look for cracks in the security of programs and use these vulnerabilities to gain access to your device. With this access, they could enable a keylogger to track what you type, steal confidential information, or even install ransomware to lock you out of your files and demand payment for access. Software developers generally fix the problem and issue a patch as soon as they find out. If your machine isn’t patched, then it is vulnerable to that flaw. The longer you wait to install the update, the longer your system is at risk.
Similarly, when a software developer says that they will stop support for a piece of software (e.g. Microsoft ceased support for Windows XP in 2014) it means any security flaws found after the date would not be patched.
Recommend that you do not use a device with outdated or unpatched software.
How do I check for software updates?
Any device that runs software, be it a computer, tablet, or even a smart tv, can release updates. Most software will prompt you when an update is available, but it’s good practice to check periodically. Here is a general guide to checking for updates on common platforms:
Mac System Updates (for macOS Catalina)
1. Open the Apple menu and select About this Mac.
2. Click Software Updates….
3. If any are available, you will have the option to install it.
Windows System Updates (for Windows 10)
1. Open the start menu and select Settings.
2. Select Update&SecuritySettings then select WindowsUpdate.
3. Click Check for Updates. If any are available, you will have the option to install it.
iOS Updates
1. Open the Settings app and tap General.
2. Tap SoftwareUpdate.
3. If any are available, you will have the option to install it.
Android Updates (for most devices running Android 10 or higher)
1. Open the Settings app and go to the System section.
2. Tap About Phone. (If this is not an option, skip to step 3.)
3. Tap System Updates.
4. Tap Check for Update. If any are available, you will have the option to install it.
Tip 13: INSTALL APPS ONLY FROM TRUSTED SOURCES
What to do:
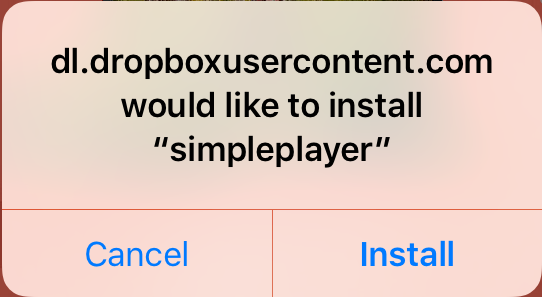
Install apps only from official app stores and official websites.
Why do it?
Fake apps or apps downloaded from other sources can contain malware and lead to theft of personal data or slowing down of your device, or both.
Avoid installing apps from prompts like this.
Tip 12: USE ANTI-VIRUS AND ANTI-MALWARE
What to do:
Purchase anti-virus and anti-malware application for your devices. If the PC is provided by your employer, do not delete or disable the security software.
Why do it?
Even if you are careful online, you may accidentally click on a link that tries to infect your device. Antivirus and anti-malware adds a layer of security to your overall cyber-security stance.
As of June 2018, PC Magazine UK rates McAfee as the best antivirus and anti-malware protection.
Tip 11: GO ANONYMOUS
What to do:
Use Private or Incognito mode on your browser, AND use a Virtual Private Network (VPN) service.
Why do it?
In Private or Incognito mode, your browser won’t save your browsing history, site data and cookies. It also won’t save the data you entered in online forms. Other people using the same device (if you were using a shared PC) won’t see your activity. However, this activity will still be visible to the websites you visit, and your internet service provider.
A VPN on the other hand provides end-to-end encryption of your activity and data. Your ISP (or that dodgy WiFi you have connected to at the cafe) won’t be able to see your traffic. Sure the website you interact with will still see your data but depending on the “exit server” you choose, it could think you’re in Frankfurt, Germany when you’re in fact in a coffee shop in Shanghai, China.
Many people use VPN to gain access to internet services such as email or video streaming services that are normally blocked or restricted locally.
Do a bit of research and choose a service you trust, and has the features and speed capability you need. Paid is better than free.
Tip 10: SAFE SURFING
What to do:
Make sure the URL is encrypted. Look for the “HTTPS”
Why do it?
A website starting with https (like this one) encrypts the data between you and the website, so that no one can eavesdrop or tamper with the data flow. If a website does not start with https, do not give them confidential info (name, address, card details, etc).
Know which links are safe and which are not – hover over a link to discover where it directs to.
Tip 9: BLOCK ONLINE ADS
What to do:
Use an AdBlocker to prevent being shown ads, and avoid possible malware infection.
Why do it?
Attackers can inject malicious code or malware-filled ads into legit online advertising networks and websites. This is called malvertising and it can infect your computer.
Some websites rely heavily on ads for revenue and ask that you sign up to their website (so they can send you marketing material), or disable the ad-blocker software. You can temporarily disable the ad-blocker for the website so you can continue to access their content. Bear in mind that your PC would be vulnerable to malvertising for the duration of the ad-blocker being disabled.
